Most of the time, you’re really not going to want to do anything written in this article since it requires looking at a lot of technical stuff, but if you think there is a program on your computer that shouldn’t be there communicating secretly on the Internet, the methods below will help you identify anything unusual. It’s worth noting that a computer running an operating system like Windows with a few programs installed will end up making a lot of connections to outside servers by default. For example, on my Windows 10 machine after a reboot and with no programs running, several connections are made by Windows itself, including OneDrive, Cortana and even desktop search. Read my article on securing Windows 10 to learn about ways you can prevent Windows 10 from communicating with Microsoft servers too often. There are three ways you can go about monitoring the connections that your computer makes to the Internet: via the command prompt, using Resource Monitor or via third-party programs. I’m going to mention the command prompt last since that’s the most technical and hardest to decipher.
Resource Monitor
The easiest way to check out all the connections your computer is making is to use Resource Monitor. To open it, you have to click on Start and then type in resource monitor. You’ll see several tabs across the top and the one we want to click on is Network.
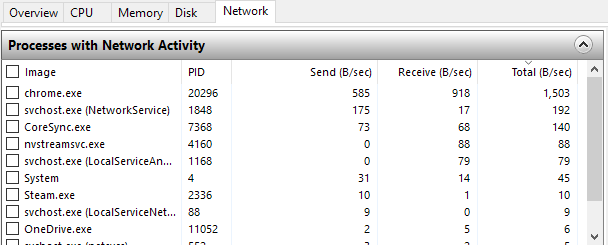
On this tab, you’ll see several sections with different types of data: Processes with Network Activity, Network Activity, TCP Connections and Listening Ports.
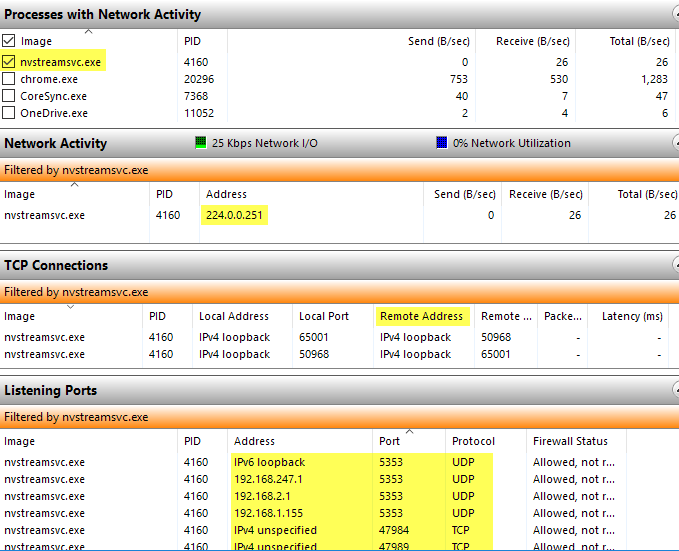
All the data listed in these screens are updated in real time. You can click on a header in any column to sort the data in ascending or descending order. In the Processes with Network Activity section, the list includes all the processes that have any kind of network activity. You’ll also be able to see the total amount of data sent and received in bytes per second for each process. You’ll notice there is an empty checkbox next to each process, which can be used as a filter for all the other sections. For example, I wasn’t sure what nvstreamsvc.exe was, so I checked it and then looked at the data in the other sections. Under Network Activity, you want to look at the Address field, which should give you an IP address or the DNS name of the remote server.
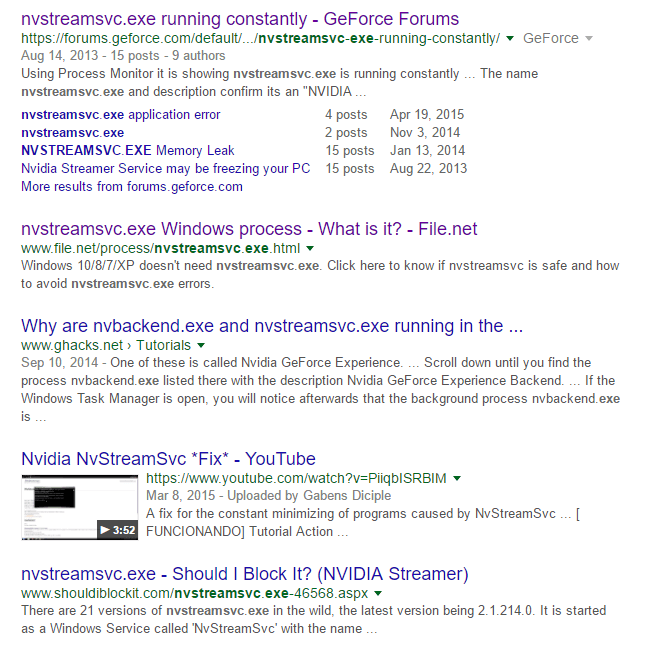
In and of itself, the information here won’t necessarily help you figure out whether something is good or bad. You have to use some third-party websites to help you identify the process. Firstly, if you don’t recognize a process name, go ahead and Google it using the full name, i.e. nvstreamsvc.exe.
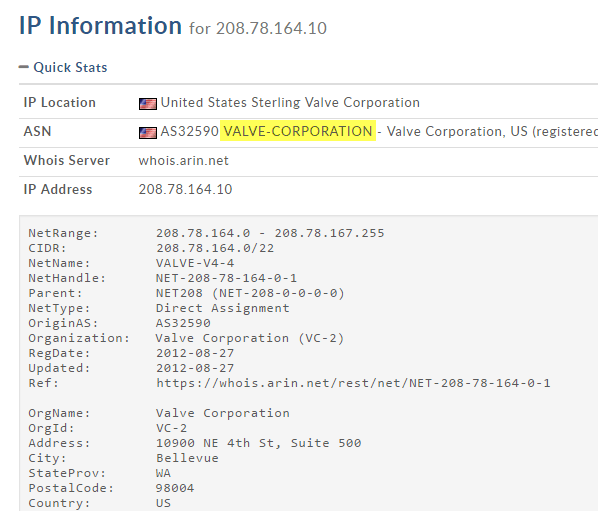
Always, click through at least the first four to five links and you’ll instantly get a good idea of whether or not the program is safe or not. In my case, it was related to the NVIDIA streaming service, which is safe, but not something I needed. Specifically, the process is for streaming games from your PC to the NVIDIA Shield, which I don’t have. Unfortunately, when you install the NVIDIA driver, it installs a lot of other features you don’t need. Since this service run in the background, I never knew it existed. It didn’t show up in the GeForce panel and so I assumed I just had the driver installed. Once I realized I didn’t need this service, I was able to uninstall some NVIDIA software and get rid of the service, which was communicating on the network all the time, even though I never used it. So that’s one example of how digging into each process can help you not only identify possible malware, but also remove unnecessary services that could possibly be exploited by hackers. Secondly, you should look up the IP address or DNS name listed in the Address field. You can check out a tool like DomainTools, which will give you the information you need. For example, under Network Activity, I noticed that the steam.exe process was connecting to IP address 208.78.164.10. When I plugged that into the tool mentioned above, I was happy to learn that the domain is controlled by Valve, which is the company that owns Steam.
If you see an IP address is connecting to a server in China or Russia or some other strange location, you might have a problem. Googling the process will normally lead you to articles on how to remove the malicious software.
Third Party Programs
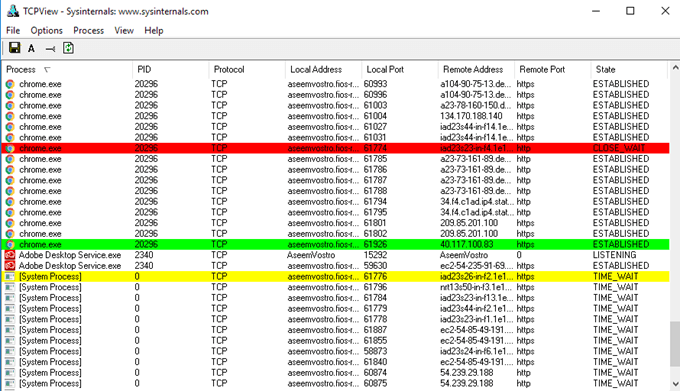
Resource Monitor is great and gives you a lot of info, but there are other tools that can give you a little bit more information. The two tools that I recommend are TCPView and CurrPorts. Both pretty much look exactly the same, except that CurrPorts gives you a whole lot more data. Here’s a screenshot of TCPView:
The rows you are mostly interested in are the ones that have a State of ESTABLISHED. You can right-click on any row to end the process or close the connection. Here’s a screenshot of CurrPorts:
Again, look at ESTABLISHED connections when browsing through the list. As you can see from the scrollbar at the bottom, there are many more columns for each process in CurrPorts. You can really get a lot of information using these programs.
Command Line
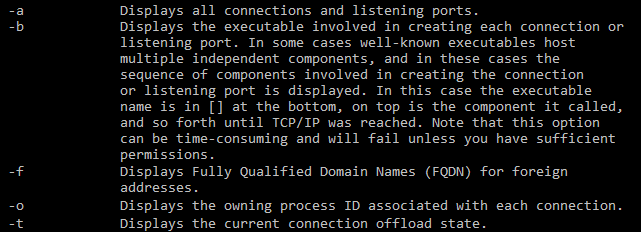
Finally, there is the command line. We will use the netstat command to give us detailed information about all the current network connections outputted to a TXT file. The information is basically a subset of what you get from Resource Monitor or the third-party programs, so it’s really only useful for techies. Here’s a quick example. First, open an Administrator command prompt and type in the following command:
Wait for about a minute or two and then press CTRL + C on your keyboard to stop the capture. The netstat command above will basically capture all network connection data every five seconds and save it to the text file. The –abfot part is a bunch of parameters so that we can get extra information in the file. Here is what each parameter means, in case you are interested.
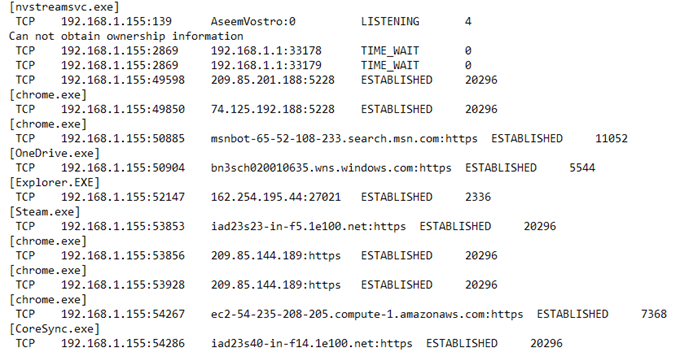
When you open the file, you’ll see pretty much the same information that we got from the other two methods above: process name, protocol, local and remote port numbers, remote IP Address/DNS name, connection state, process ID, etc.
Again, all of this data is a first step to determining whether something fishy is going on or not. You’ll have to do a lot of Googling, but it’s the best way to know if someone is snooping on you or if malware is sending data from your computer to some remote server. If you have any questions, feel free to comment. Enjoy!